H4ck1ng G00gl3 ep003 challenge 03
Introduction
H4ck1ng G00gl3 is a series of security challenges published on October 2022 where the only way to win is to think like a hacker. In this post, I explain how I solved ep003 challenge 03. Category Android.
Learning Journey
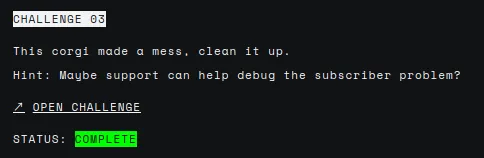
Opening the challenge gives us a zip containing two files: an apk and a QR code. First things first, let’s install the application and see if we can scan the QR code and what’s the result.

The QR code returns the Secret flag data. However, it seems like we have to be a subscriber to get the URL field where I guess the flag is hidden. I’m pretty sure we can modify the apk in a way that shows us the flag. To do that, we have to obtain the source code first. There is a tool called dex2jar that extracts the jar file from the apk.
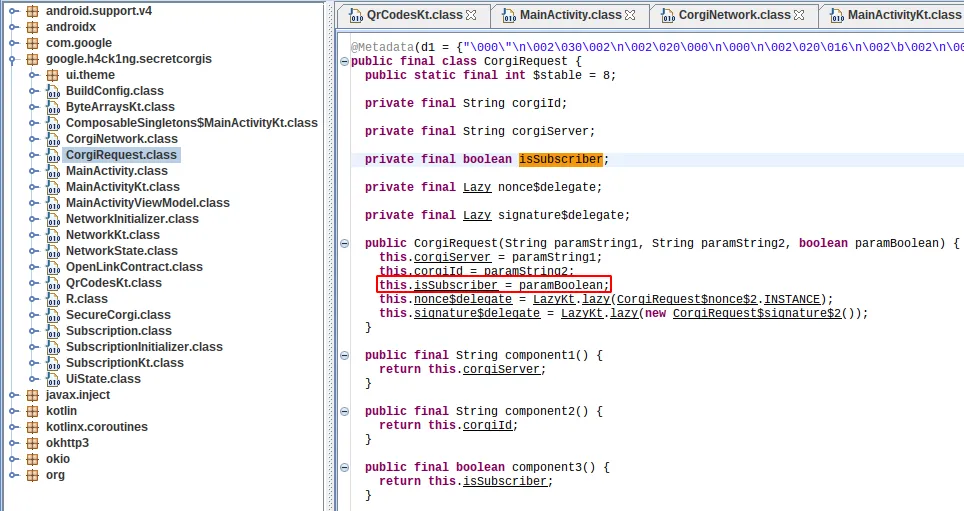
Then, we can use jd-gui to open the jar file and look at the source code. Once we have it, there is no trick. We have to read it and find where the vulnerability is. In that case, I found the signature of the HTTP request was different between a subscribed and an unsubscribed user.
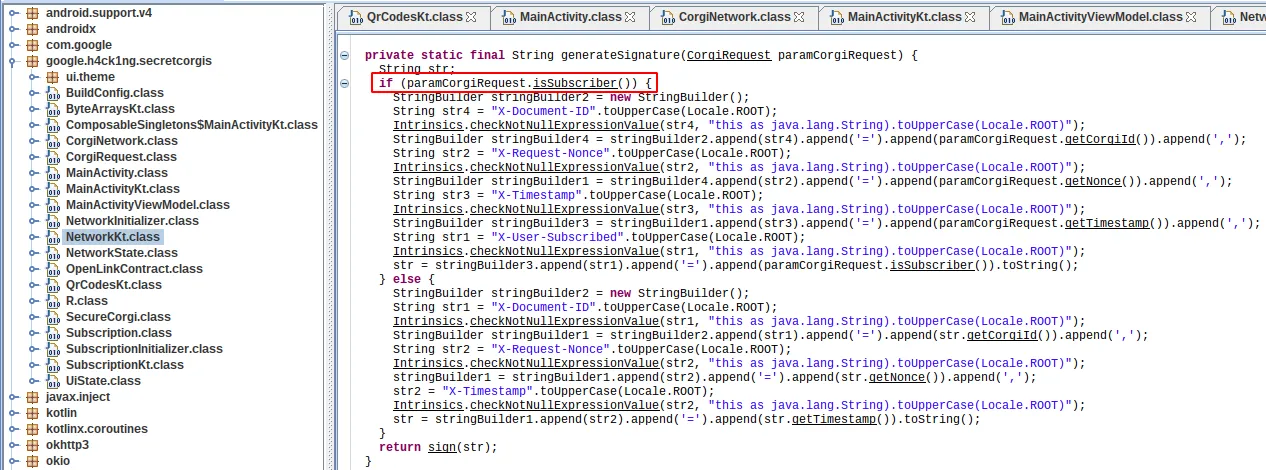
I wondered how the application knew if a user was a subscriber. After searching through the code, I found the “CorgiRequest” class with the “isSubscriber” field, initialized in the constructor. In other words, if we set the “isSubscriber” field to true when the class is created, we might get the flag.
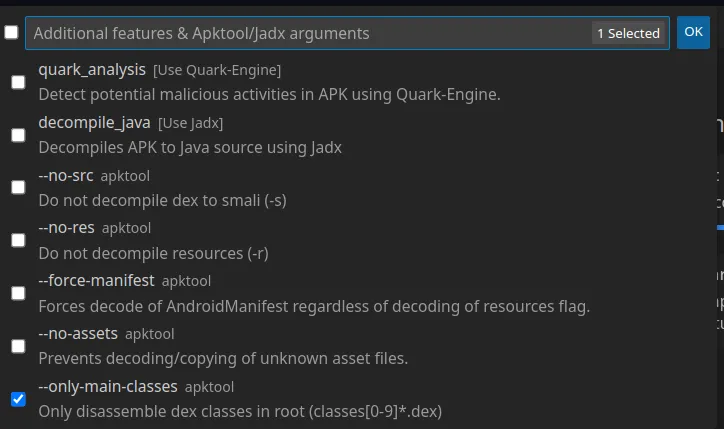
To modify the application, we are going to use the APKLab VsCode plugin. First, we are going to decompile it.
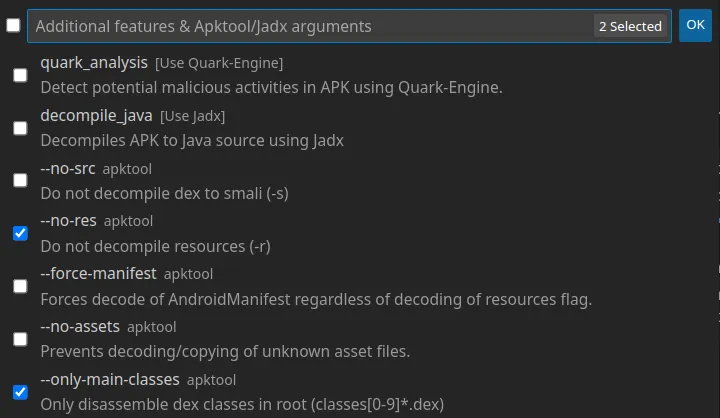
Decompiling the resources gave me an error, so I tried decompiling all except the resources.
After decompiling it, we will have access to the code in the Smali language. It’s a low-level language, and it’s harder to understand. We know we have to modify the constructor class of the CorgiRequest class. For that challenge, the change is tiny.
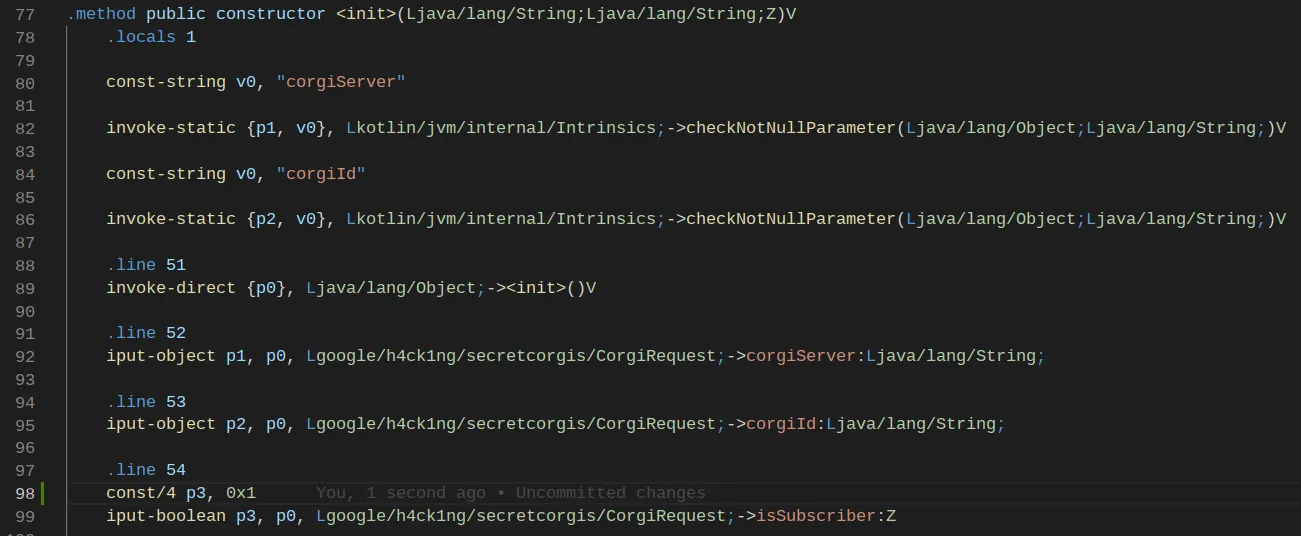
Now we need to recompile the code into an apk and sign it.
The last step is to install this new apk and run it. Now, the flag will appear after scanning the QR code. With that, we completed the challenge.
