H4ck1ng G00gl3 ep003 challenge 02
Introduction
H4ck1ng G00gl3 is a series of security challenges published on October 2022 where the only way to win is to think like a hacker. In this post, I explain how I solved ep003 challenge 02. Category Escape Restricted Shell.
Learning Journey
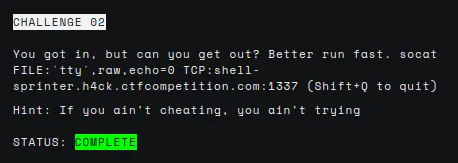
The description gives us the command to connect to a remote machine.
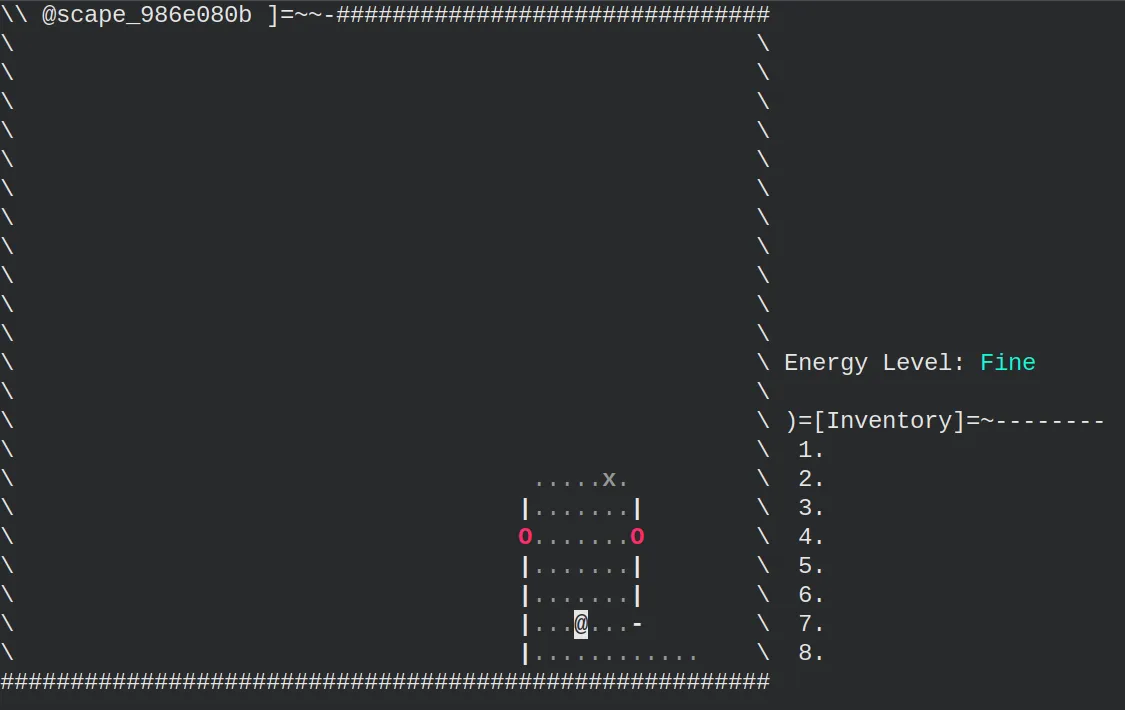
At this point, we can try winning the game or cheating, as the hint suggests. At first, I tried to play the game for a while, searching for clues on how to cheat it. I could not find a way. I was recovering a lot of coordinates and images that didn’t make sense and didn’t help me. Later I learned that they are related to the bonus challenge for this episode. After dying a couple of times, the game became tedious, and I didn’t find a way to cheat. I asked the community for help. The hint is related to the famous Konami cheat code. After introducing it, we get to another screen where we can input text.
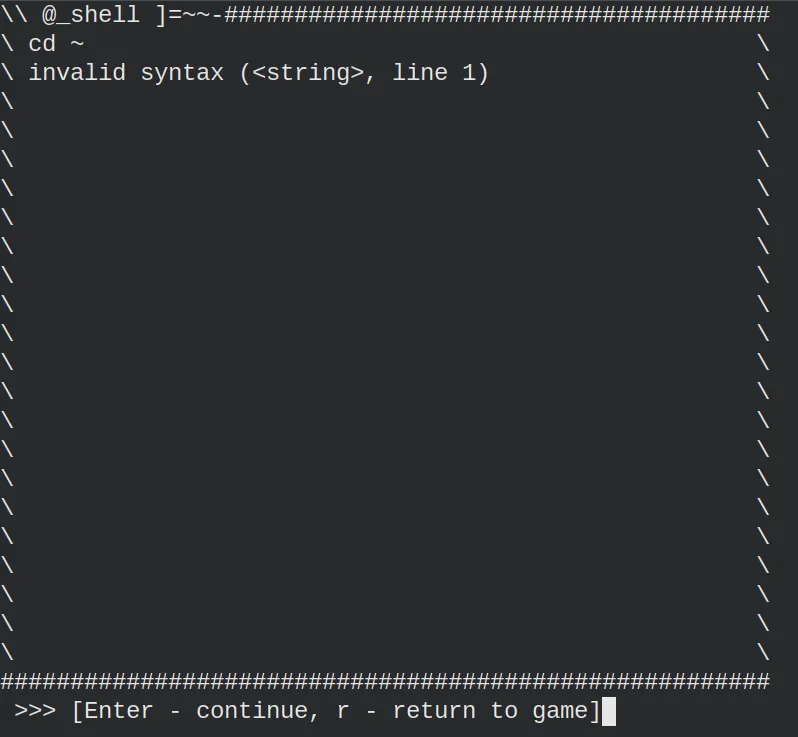
Notice that it won’t execute any command. We need to do some research. First, I copied the error output of the command “cd ~” into the Google search engine.
We can try to execute a python function to check if it’s a python shell and its version. In that case, I decided to call:
print "asd"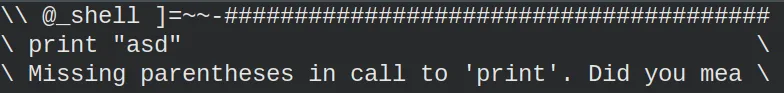
By the given output, we can see that the shell is running python version 3. Lucky me, I found a webpage with tricks to scape from restricted python3 shells. That page shows how to access the builtins module, for example.
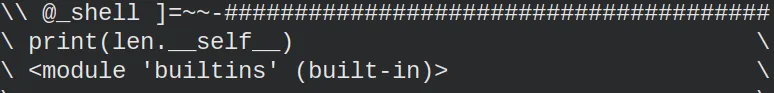
The builtins module gives access to several functions, one of them being the open function. That means that we can open a file and read it. We know from past challenges that the flag file is at the root directory, and therefore, we can get the flag with
print(len.__self__.open('flag').read())With that, we completed the challenge.
