H4ck1ng G00gl3 ep003 challenge 01
Introduction
H4ck1ng G00gl3 is a series of security challenges published on October 2022 where the only way to win is to think like a hacker. In this post, I explain how I solved ep003 challenge 01. Category Misc.
Learning Journey
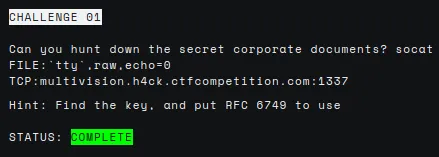
The description tell us how to connect to the machine with socat. However, it requires a password. I tried to guess it with no luck. I watched the episode video again but didn’t find anything interesting. I even tried searching for vulnerabilities or brute force scripts targeting socat. Nothing of that worked. I asked the community for a hint. They told me to check the intro tab of the episode.
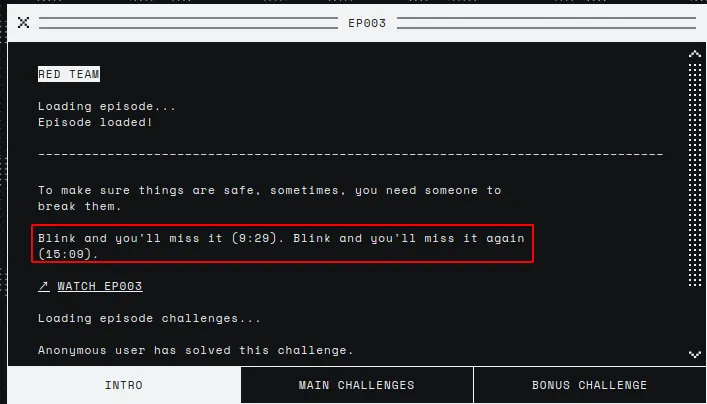
I believe I never read the introductions to the different challenges, but it was necessary this time. There, we can see two times at which the episode video might show something interesting. If we stop the episode at 15:09 we will see the password.

We can access the machine now.
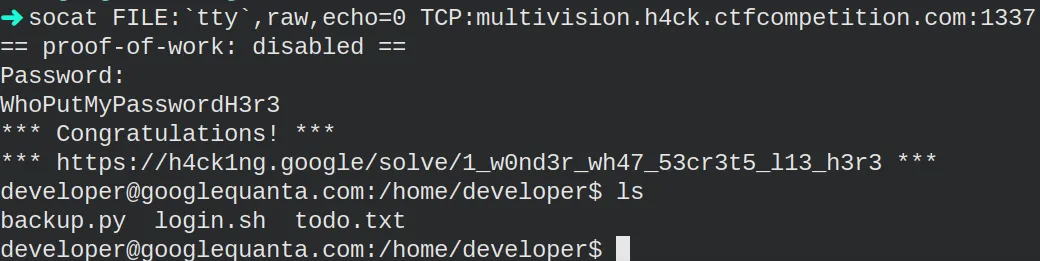
In the home directory, we find three files: backup.py, login.sh and todo.txt. The login.sh contains the code executed when connecting with socat, nothing of interest. However, the other two files contain relevant information. I decided to check the backup.py first.
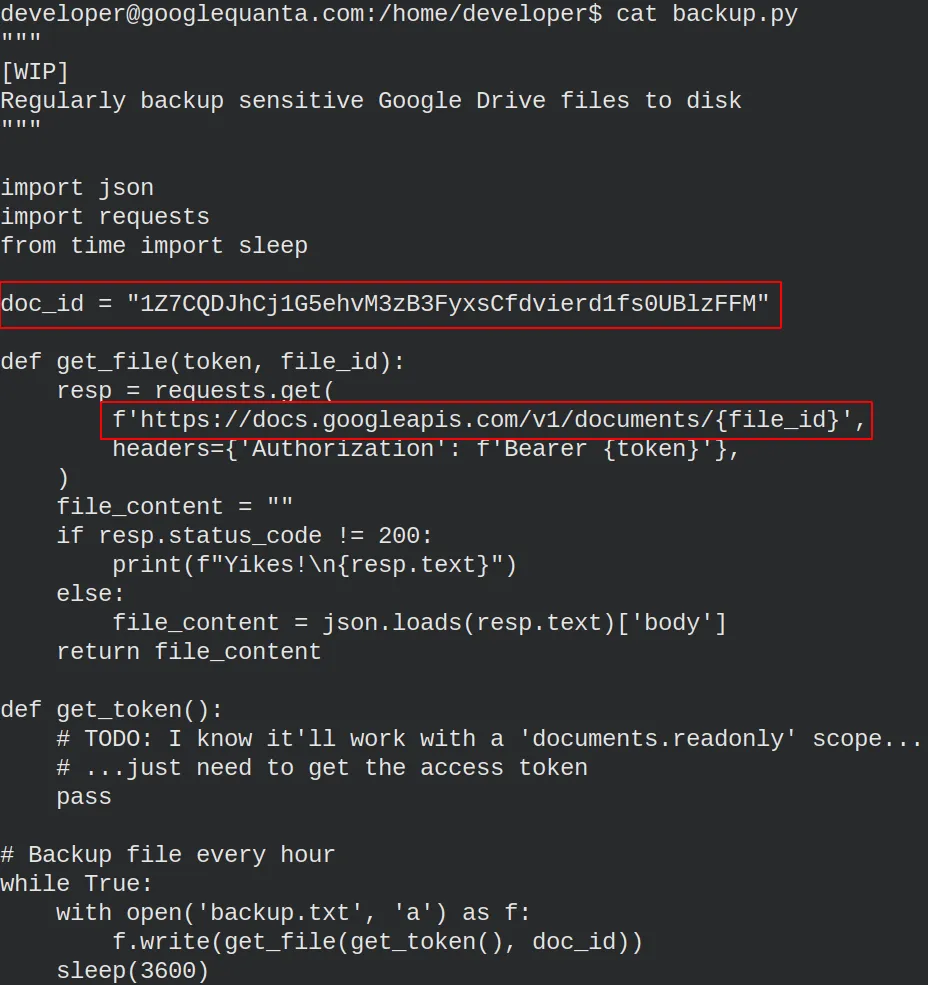
It’s a simple unfinished script. The script creates the backup of a
document, probably the one we need to get. The problem is that we need
an access token to get the file. Unlucky for us, the function that
gets the token hasn’t been implemented. In any case, we can see framed
in red the base URL and the document id. Hence, we know the document is
at
https://docs.googleapis.com/v1/documents/1Z7CQDJhCj1G5ehvM3zB3FyxsCfdvierd1fs0UBlzFFM.
Besides, we have to use RFC 6749: The OAuth 2.0 Authorization
framework. We know it from the challenge hint,
Hint: Find the key, and put RFC 6749 to use. That means we need to get
the access token using the OAuth 2.0 framework. I wrote this
down and kept collecting information.
I opened the todo.txt file and saw the following:
Today
[x] Added backup-tool@project-multivision.iam.gserviceaccount.com with viewer-access to super sensitive design doc
[x] Tried activating service account with gcloud, but didn't give me a documents.readonly scope
[x] Cleaned up service account key from disk before signing off
Tomorrow
[] Finish writing Google Drive backup scriptWe can read that the developer used a service account with gcloud. He also mentions something about a “documents.readonly” scope and that he removed the key from the disk. That is unfortunate because we need it to get the access token.
At this point, I did not know what to do or how to proceed. I read diagonally the RFC 6749 and searched for information about OAuth2.0 on internet but did not find anything that could help me. For no reason, I thought it was worth returning to the developer machine to navigate the directories and see if I could find anything. After some time, I found something that caught my attention. A hidden folder named “.config”.
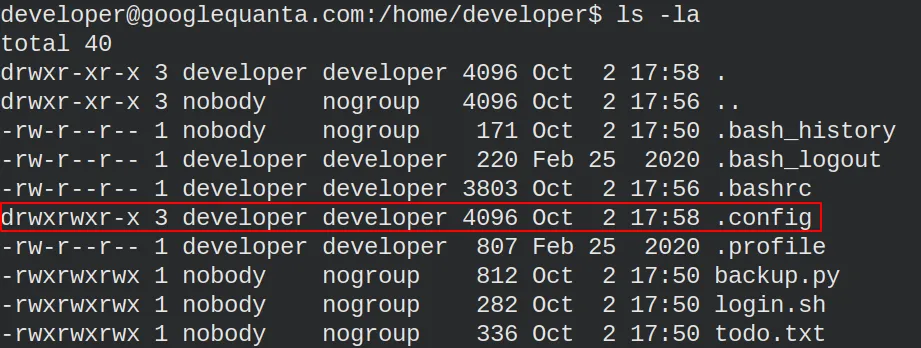
This folder contains a gcloud folder with promising files.
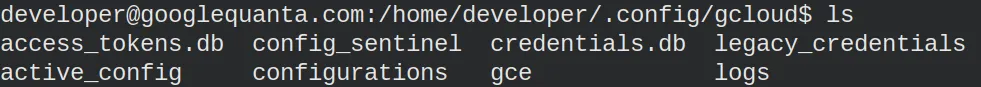
Remember that we needed an access token? Well…, there we have a access_tokens.db, which includes an old access token and a JWT.
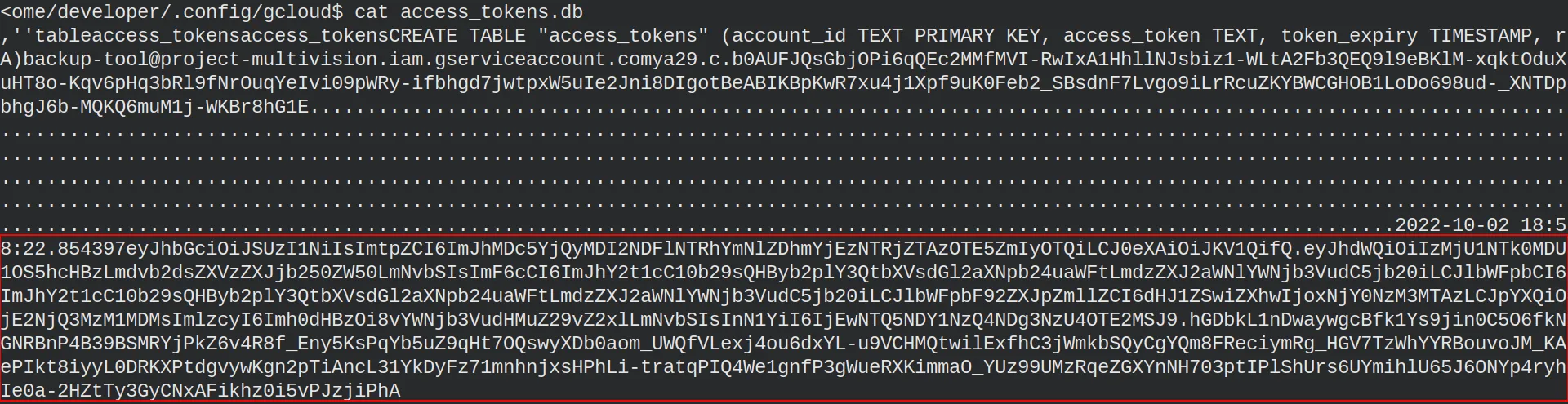
We can paste the token into the https://jwt.io/ webpage and see which information is inside.
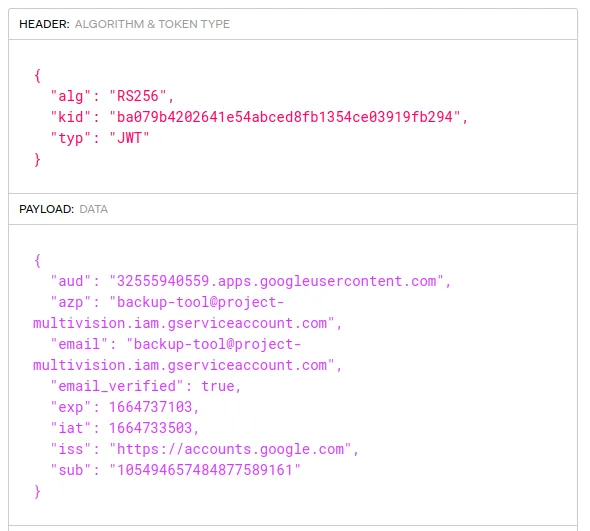
We are progressing. Still, we don’t know the information we have to include in the JWT to get a new access token, and we don’t have the private key to sign it. I returned to the .config/gcloud folder to search for the private key. There, we see a file called credentials.db, which contains the private key and the token URI, among other information we don’t need.
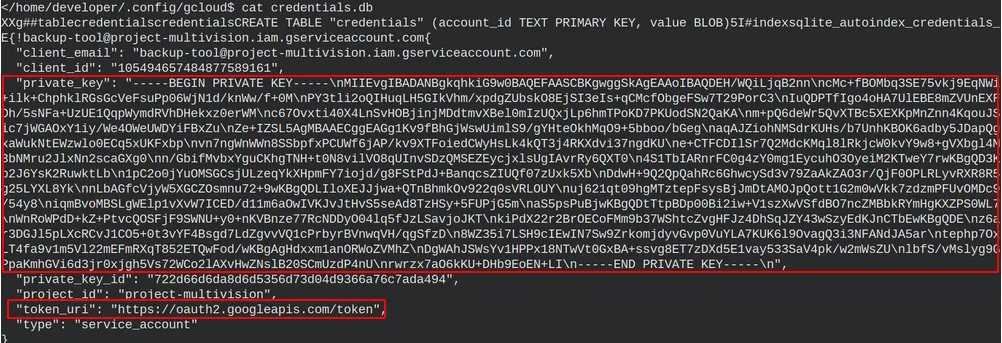
Now we have all the required information.
- JWT with some information
- Private key to sign the token
- document URL
- Token URI to get the access token
- The backup is done with a service account
- The scope is related to documents.readonly
We only need to find the correct steps we have to follow to get a valid access token and eventually get the document. After wandering through several blogs, tutorials, videos and documentation, I found some Google documentation explaining how to use OAuth 2.0 for Server to Server Application. There, we can see the information the access token must contain and how to send the POST request. First, we have to build a valid access token.
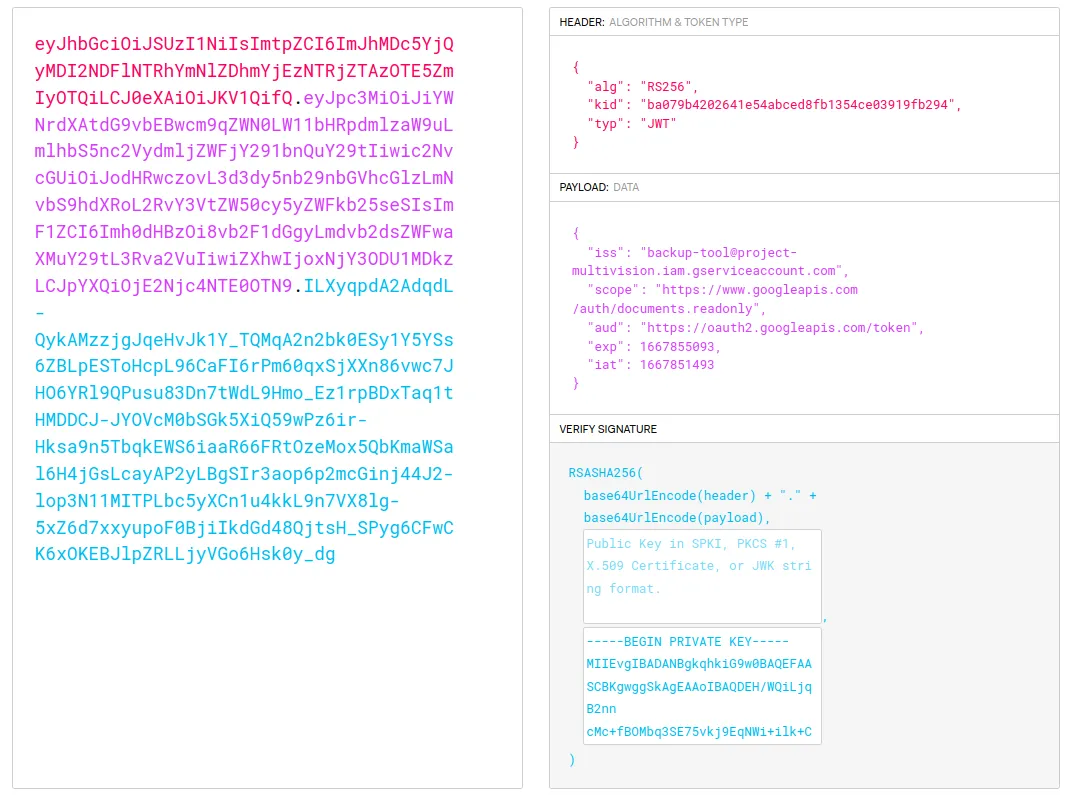
The header stays the same. However, we needed to modify the payload. The iat field timestamp is the current timestamp, and the exp field timestamp is one hour from now in the future. Moreover, we initially set the scope field to “https://www.googleapis.com/auth/documents.readonly”. We can see the different authorization scopes available for a document GET request at https://developers.google.com/docs/api/reference/rest/v1/documents/get. We are now in good shape to send a POST request to get a valid access_token.
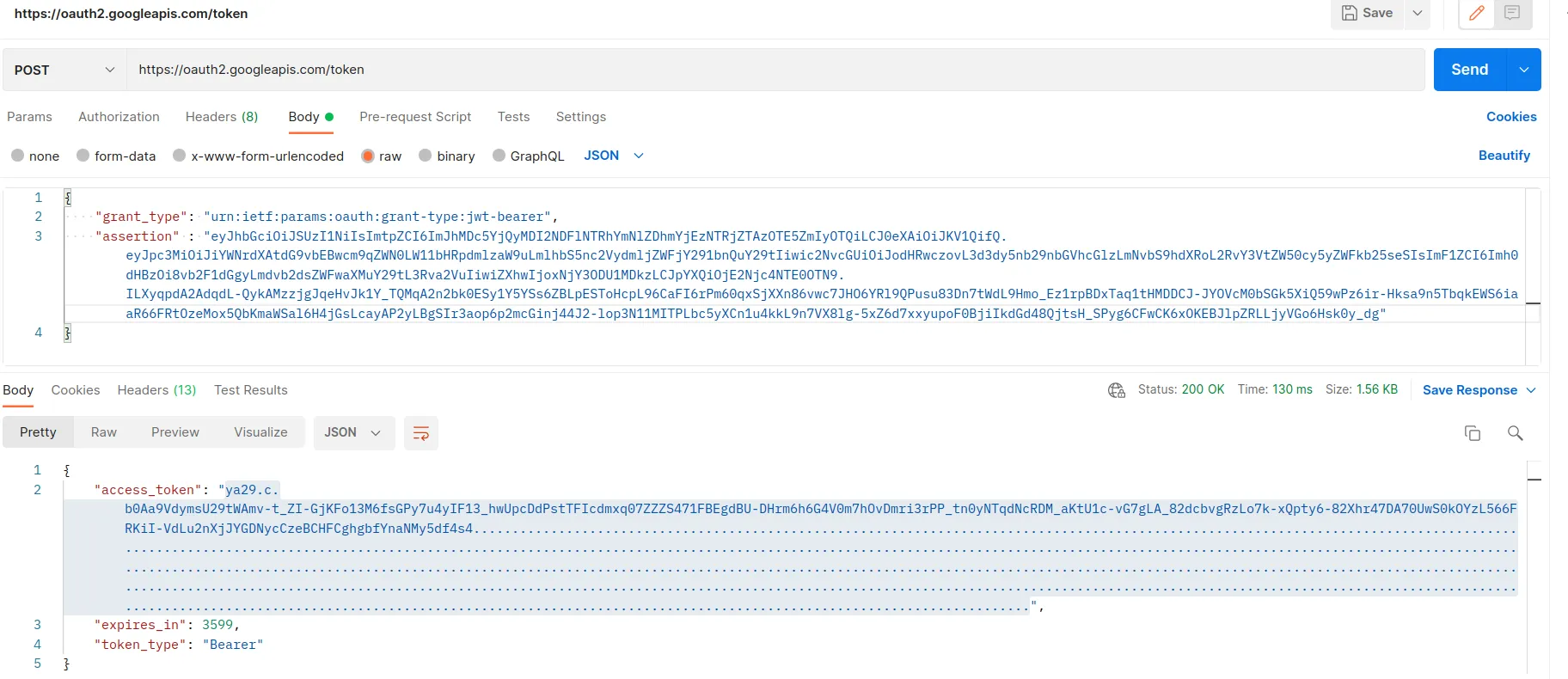
Great, we got a new access token! The last step is sending a GET request to the document URL with the access token in the Authorization header.
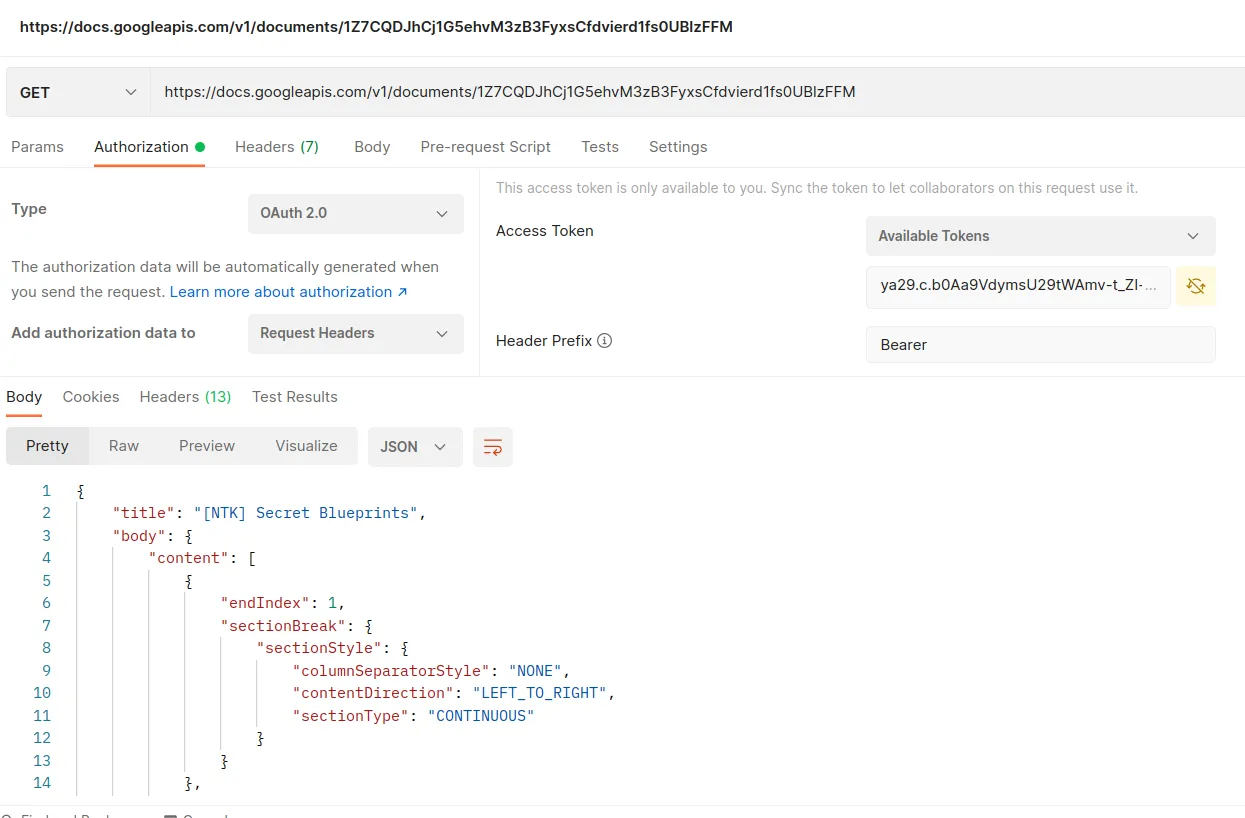
Perfect! We received the response with the blueprints! Finally, we need to search for the flag in the response. With that, we completed the challenge.
