H4ck1ng G00gl3 ep002 challenge 01
Introduction
H4ck1ng G00gl3 is a series of security challenges published on October 2022 where the only way to win is to think like a hacker. In this post, I explain how I solved ep002 challenge 01. This challenge is about Steganography.
Learning Journey
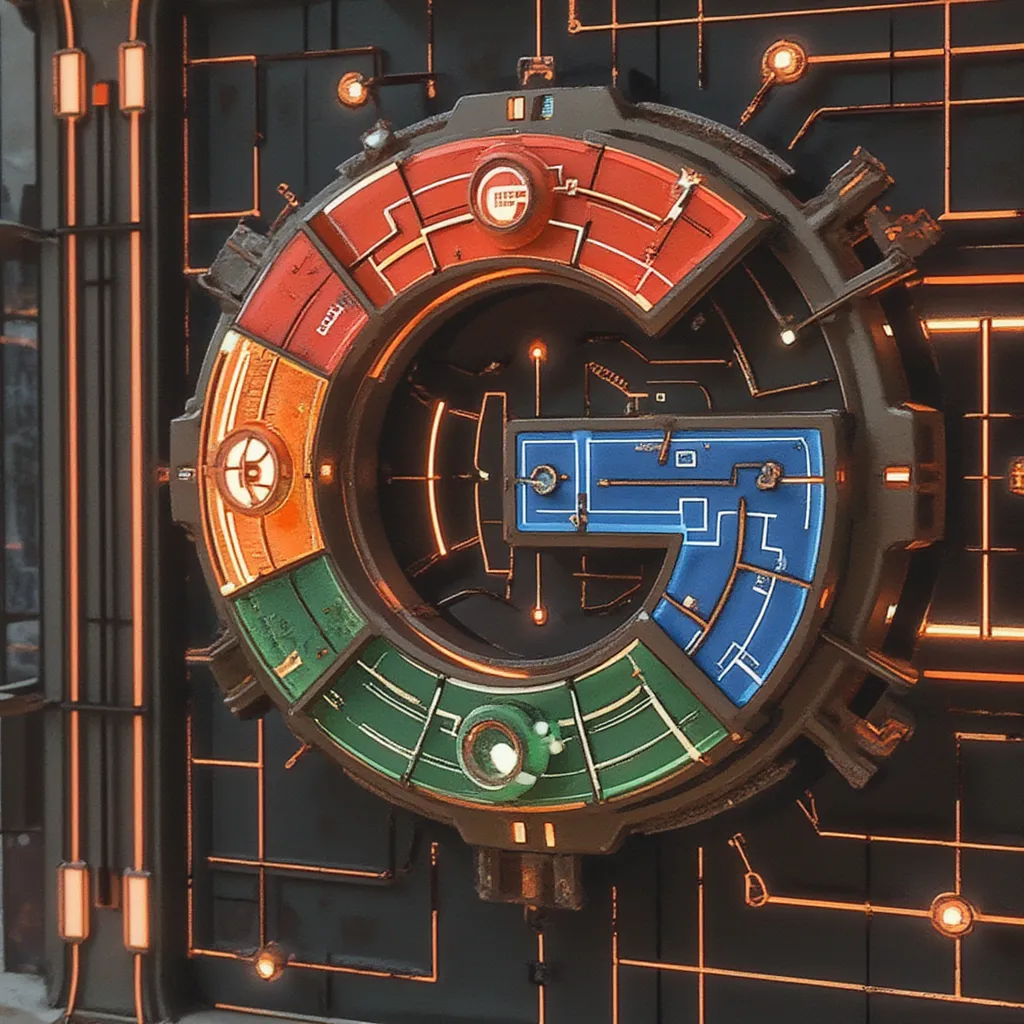
The challenge gives us the following image.

It’s an RGBA file.
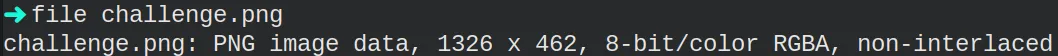
The first thing that came to mind with my basic knowledge of image steganography was the LSB (i.e. Least-Significant Bit) technique. I tried tens of different already built scripts and online tools. But I couldn’t find anything interesting. After a couple of hours, I started to doubt if I was going down the rabbit hole. I reread the hint but got no clue on how to proceed. It was time to ask the community for help.
The community pointed me to the hint:
Sometimes the answers are hidden in plain site. Also, they told me to
take a look at the main webpage background. We can see the same image. I
downloaded it and extracted the strings, which got me the following.
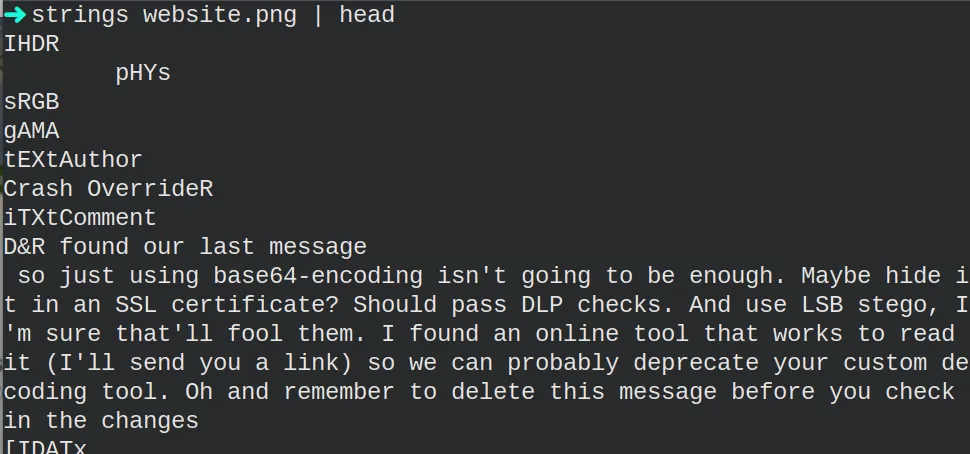
Here, we have some information.
- The information is hidden inside an SSL certificate
- LSB steganography technique is used
- The attackers used an online tool
After all, I was right about the LSB technique. Why couldn’t I get anything with the myriad of tools I used? I don’t know. I decided to write my own script.
import sys
import numpy as np
from PIL import Image
img = Image.open('challenge.png', 'r')
pixels = np.array(list(img.getdata()))
rgba_values = [values for pixel in pixels for values in pixel]
least_significant_bits = ''.join([bin(value)[-1] for value in rgba_values])
hidden_bytes = [least_significant_bits[i:i+8] for i in range(0, len(least_significant_bits), 8)]
hidden_message = [chr(int(byte, 2)) for byte in hidden_bytes]
print(''.join(hidden_message))I was finally able to get something.
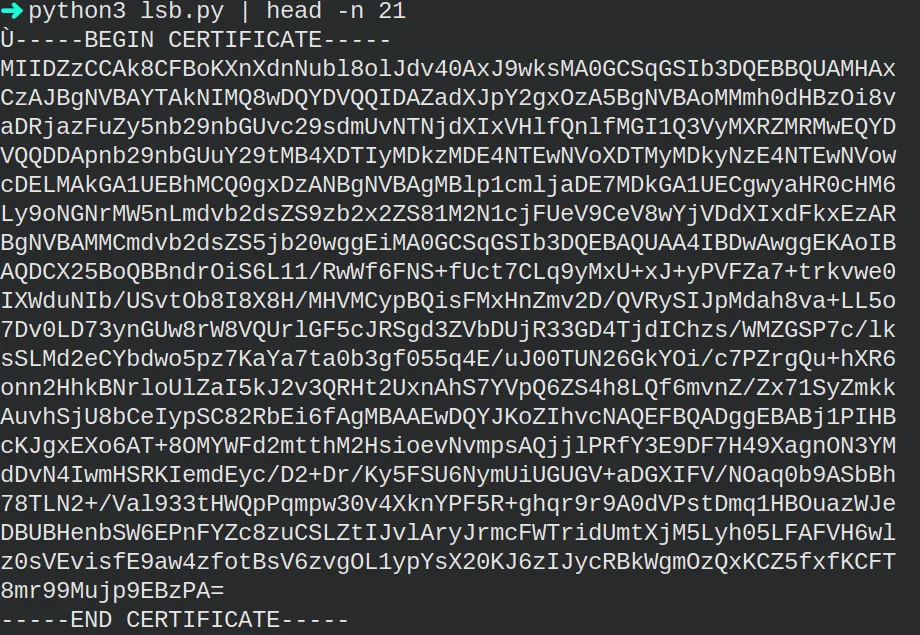
The next step was getting the flag from the certificate. I saved the result from the script into a file called “certificate.ssl” and executed the following.
openssl x509 -text -noout -in certificate.sslAfter getting the output, we can see the flag in the issuer field. With that, we completed the challenge.
